Terraform with AWS -Setup AWS IAM
How to setup AWS IAM with terraform

Photo by Soliman Cifuentes on Unsplash
Prerequisites
AWS account (free tier)
Install terraform
Install aws-cli
Configure AWS on machine as
access_key, secret_keyandregion
Scopes:
Create IAM users
Create IAM policies
IAM group
Terraform Intro
“HashiCorp Terraform is an infrastructure as code tool that lets you define both cloud and on-prem resources in human-readable configuration files that you can version, reuse, and share.” more detail about terraform here
Let’s create IAM user
Run terraform command
terraform init
terraform fmt
terraform validate
terraform plan

$ terraform apply
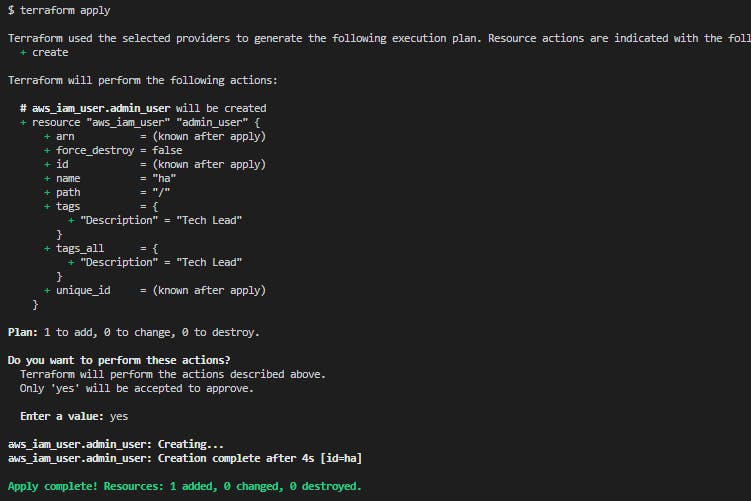
Check IAM list with aws-cli command
$ aws iam list-users

Ok. user has been created with terraform. then we will create iam policies to user was created.
Create IAM policies with terraform
create iam policy, then attach policy to user
- create admin-policy.json file
above file is policy to user was created
- Run terraform again
$ terraform plan

$ terraform apply
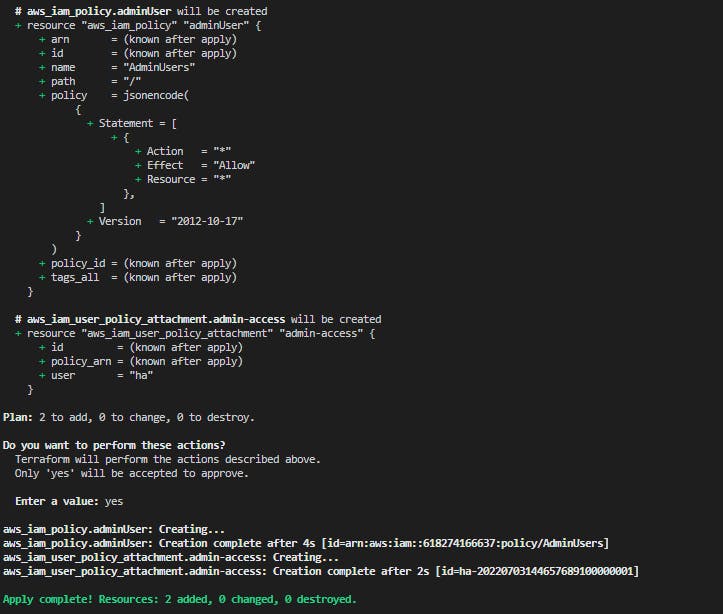
Check IAM policies
$ aws iam list-attached-user-policies --user-name ha
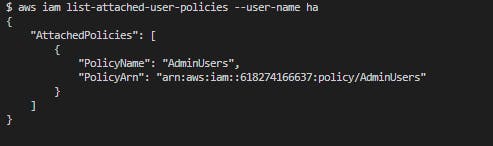
IAM policies has been created. Then we will update user to use password.
Add user login profile
useaws_iam_user_login_profile resource.
...
resource "aws_iam_user_login_profile" "userLogin" {
user = aws_iam_user.admin_user.name
}
output "password" {
value = aws_iam_user_login_profile.userLogin.password
}
...
- run terraform plan and apply again.
$ terraform plan
$ terraform apply --auto-approve

We can login to AWS dashboard. Don’t share your password. for safe you can use PGP to encrypt the password.
To destroy IAM user we can use terraform destroy
$ terraform destroy --auto-approve
to make sure user was deleted we can check user with aws-cli command
$ aws iam list-users
Full Code for IAM user:
Create IAM with multiple users
How to create multiple users with terraform?
OK let’s we create:
- create variable, variable.tf
The above we make three users with named “ha”, “lucy”,”john”. We will use for_each on terraform, more detail about for_each here.
update main.tf file as below:
resource "aws_iam_user" "admin_user" {
name = each.value
for_each = toset(var.admin_users)
tags = {
Description = "Tech Lead"
}
}
resource "aws_iam_user_login_profile" "userLogin" {
for_each = aws_iam_user.admin_user
user = each.value.name
}
resource "aws_iam_policy" "adminUser" {
name = "AdminUsers"
policy = file("admin-policy.json")
}
resource "aws_iam_user_policy_attachment" "admin-access" {
for_each = aws_iam_user.admin_user
user = each.value.name
policy_arn = aws_iam_policy.adminUser.arn
}
output "password" {
value = {
for k, v in aws_iam_user_login_profile.userLogin : k => v.password
}
}
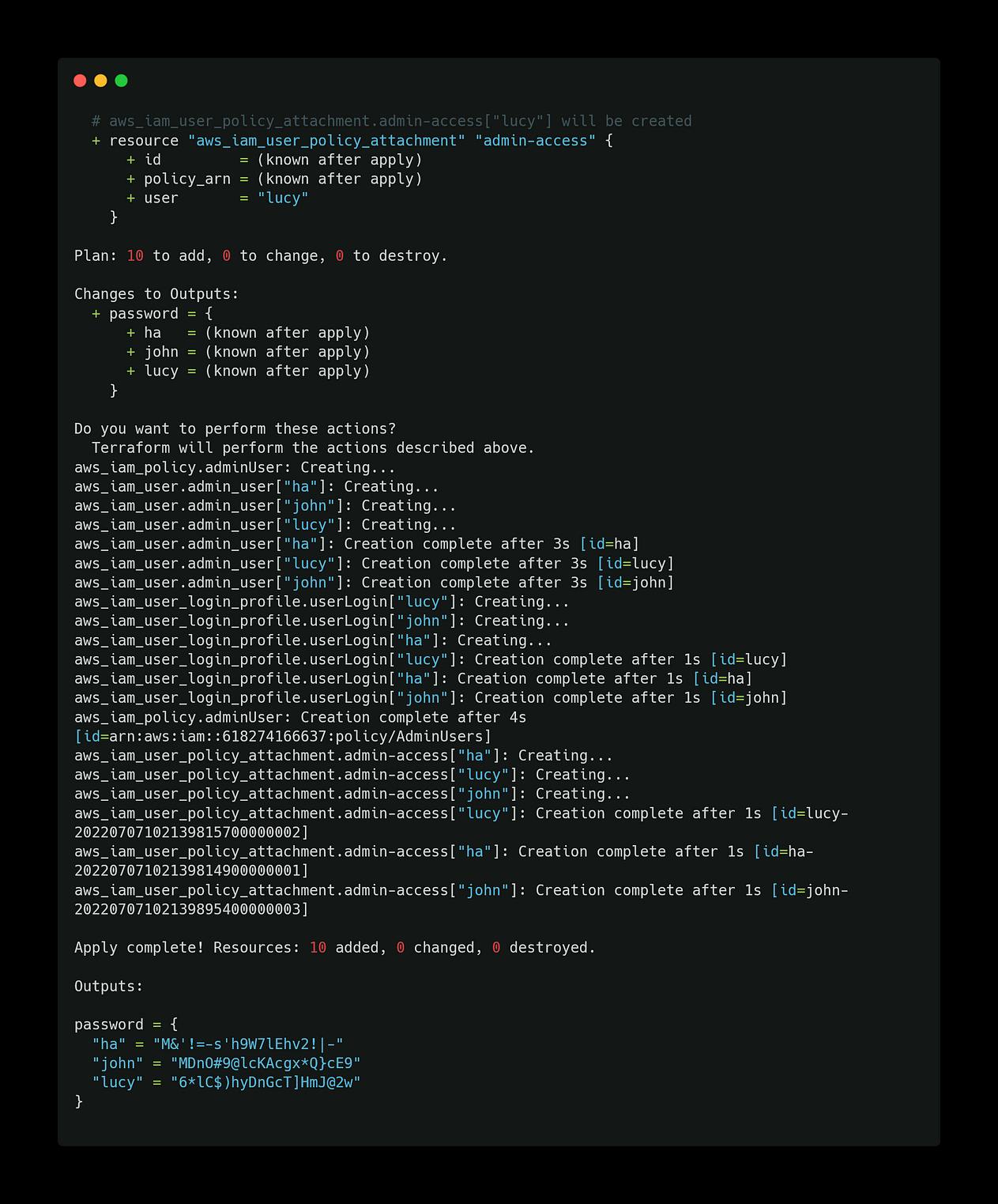
check with aws-cli command
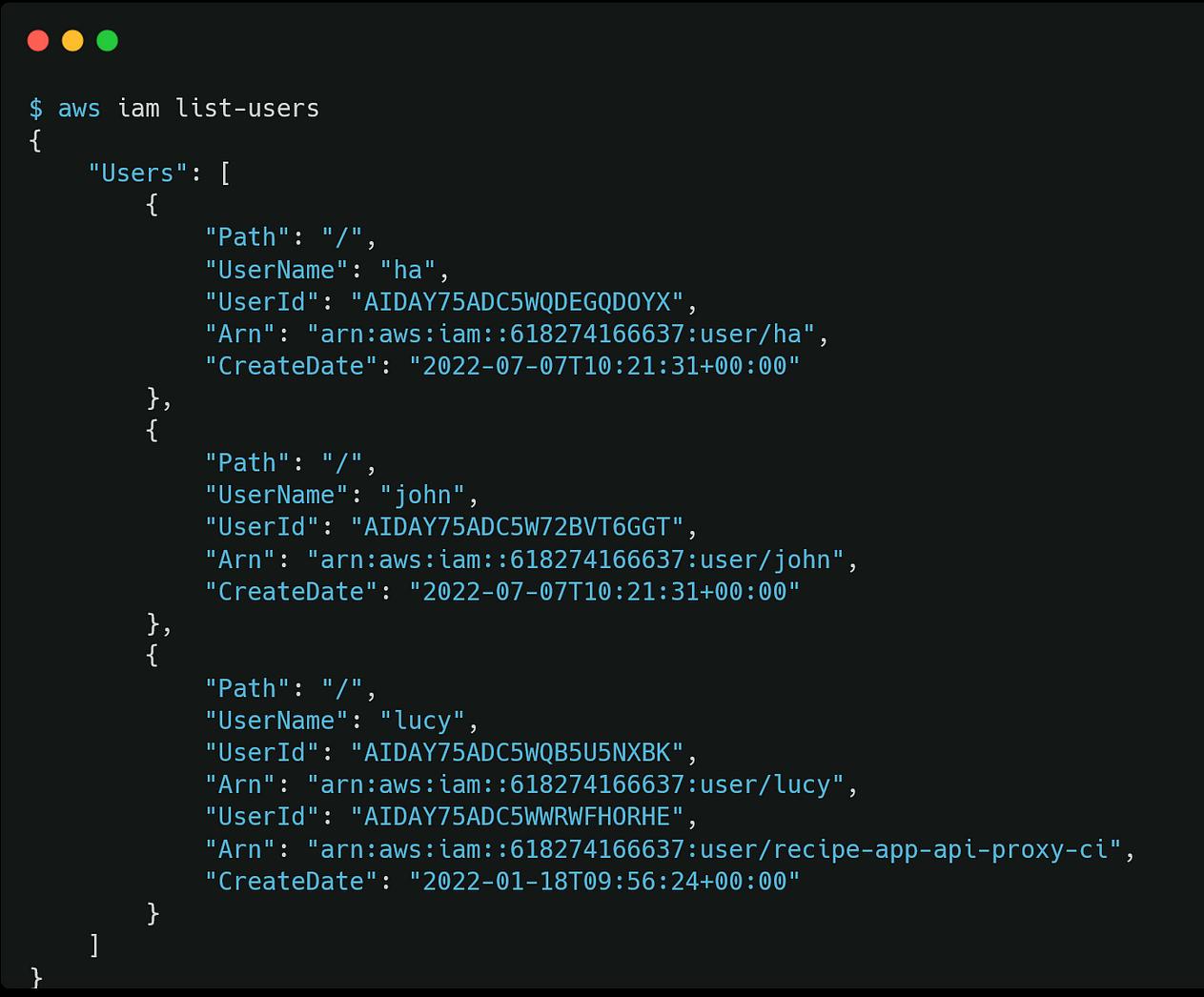
ok, try to login with dashboard. Don’t share your password. To destroy the resource use this command:
$ terraform destroy
Full Code for IAM users:
resource "aws_iam_user" "admin_user" {
name = each.value
for_each = toset(var.admin_users)
tags = {
Description = "Tech Lead"
}
}
resource "aws_iam_user_login_profile" "userLogin" {
for_each = aws_iam_user.admin_user
user = each.value.name
}
resource "aws_iam_policy" "adminUser" {
name = "AdminUsers"
policy = file("admin-policy.json")
}
resource "aws_iam_user_policy_attachment" "admin-access" {
for_each = aws_iam_user.admin_user
user = each.value.name
policy_arn = aws_iam_policy.adminUser.arn
}
output "password" {
value = {
for k, v in aws_iam_user_login_profile.userLogin : k => v.password
}
}
- admin-policy.json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
]
}
variable "admin_users" {
type = list(string)
default = ["ha", "lucy", "john"]
}
Setup IAM Grup
- update main.tf file. add
aws_iam_groupandaws_iam_group_membershipresource.
resource "aws_iam_group" "tech-lead" {
name = "Tech-Lead"
}
resource "aws_iam_group_membership" "team" {
name = "tech-lead-group-membership"
for_each = aws_iam_user.admin_user
users = [each.value.name]
group = aws_iam_group.tech-lead.name
}
- terraform plan
$ terraform plan
- terraform apply
$ terraform apply --auto-approve
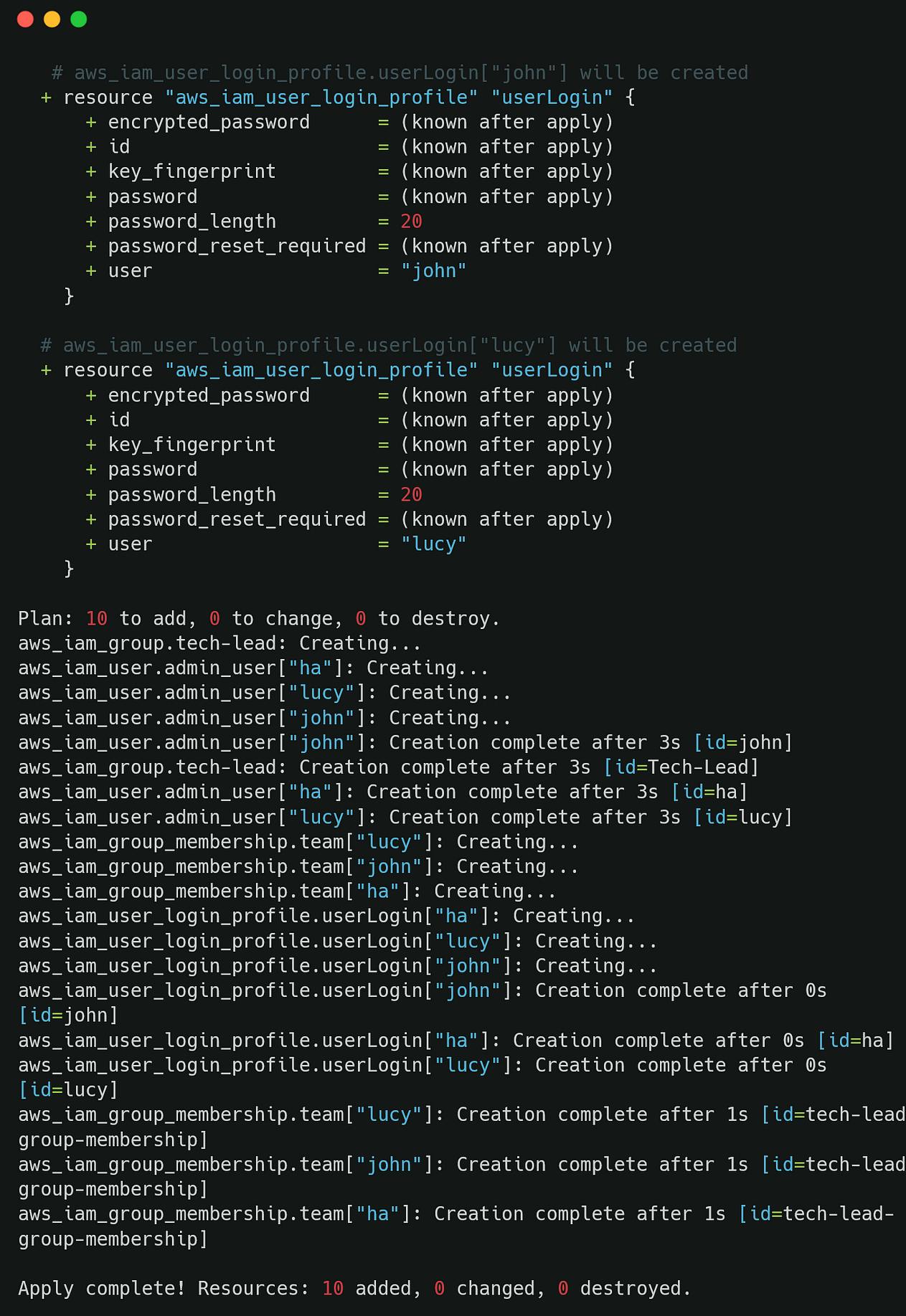
- add group policy attachment
resource "aws_iam_group_policy_attachment" "tech_lead_group_policy" {
group = aws_iam_group.tech-lead.name
policy_arn = aws_iam_policy.adminUser.arn
}
- terraform plan
$ terraform plan
- terraform apply
$ terraform apply --auto--aprove

- Check iam user with root account in AWS dashboard.
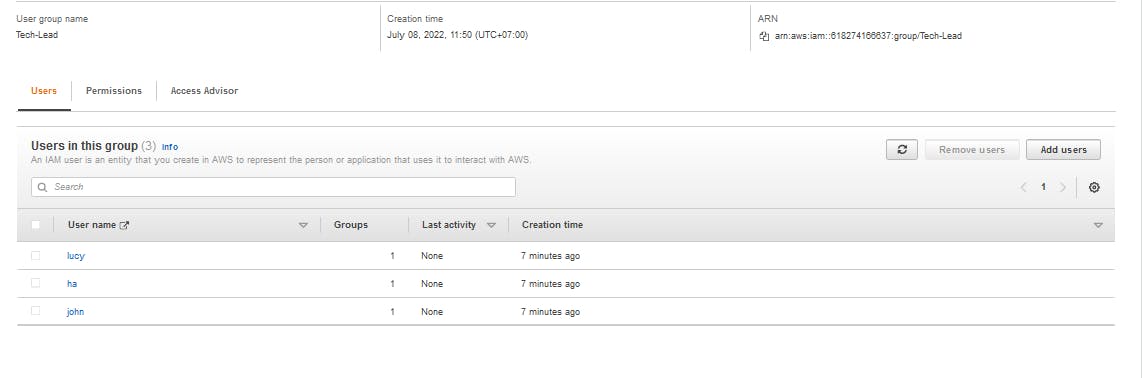
To destroy resources, run terraform destroy
$ terraform destroy
Full Code for IAM group:
Repository:
https://github.com/ahakimx/terraform-aws
References:
https://developer.hashicorp.com/terraform/language/meta-arguments/for_each
https://registry.terraform.io/providers/hashicorp/aws/latest/docs/resources/iam_user
